Introducing high-level tips and security best practices
It is hard to recover from a hack that breaches digital assets. It is bothersome to users of the blockchain platform. However, familiarity and applications of security best practices it is a sure-shot game changers. Knowing the types of crypto wallets and practical tips to protect them will curb security breaches.
Let’s get started. The following feature is designed to explain:
- What are crypto wallet types and how do they work?
- Security risks and overcoming challenges
- Potential attacks and malware that steal assets
- Best practices to mitigate the vulnerability
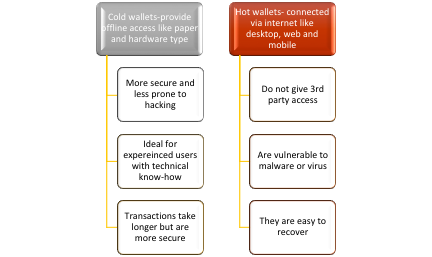
As blockchain platforms evolve, the types of crypto wallets have multiplied. They give a chance to use the platform for trading and doing business with software or a hardware device. Broadly they are divided into online (hot) or offline (cold) types depending on internet usage. The custodial type allows users to hold private keys. The non-custodial type permits a 3rd party to stash the key. Wallets are found in diverse forms like paper, web, desktop and hardware. All of them help users to spend, swap and store critical digital assets.
To make sense of the one that is suitable to you check this chart.
As crypto currencies come center stage a user can transact in different formats offered by the exchanges. All users have private and public keys (also called codes) for operations. These wallets work when bitcoin or dogecoin or any other digital currency is added after a transaction. The codes come as a string of letters and numbers to the user.
It looks like this
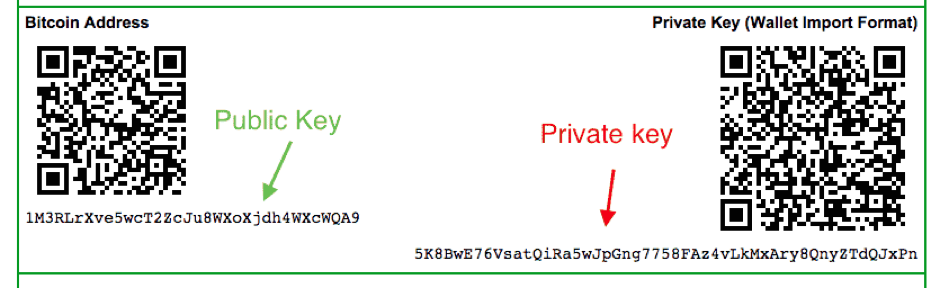
Image credit: https://99bitcoins.com/how-to-safely-deposit-and-withdraw-bitcoins-from-a-paper-wallet/
Any crypto wallet is like an email account. When you need to send money or receive money the keys are shared. Just like in an email, no passwords are shared. This is just an initial level of safety and checking the balance of the wallet.
Security risks and overcoming challenges
Once you are aware of the potential risks you can focus on doing business safely. There are risks with hot and cold wallets. As there are different types of wallets the challenges are equally diverse. The cyber threat environment is evolving and being updated is the only solution to protect the virtual wallet. Using an escrow system is safe but there are dangers and threats to ward off. It is good to study the wallet type and its reliability.
The following factors are important to enhance security.
- Private keys have to remain in an encrypted format.
- Add features like fingerprint authentication and PIN access if the storage is on the mobile phone.
- Always have strong passwords.
- Be aware of any unusual activity that could be a sign of a breach.
These are just a few ways to minimize the challenges.
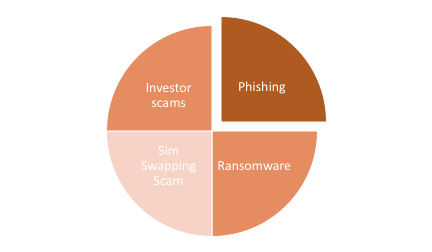
Potential attacks and malware that steal assets
Since April 2023, Rilide is the latest malware that targets crypto wallets. It targets chromium-based browsers by taking away sensitive information. It was only two months ago that Clipper malware was involved in a fake browser called Tor. Around USD 400. 000 have been stolen as cybercriminals become more sophisticated in their attempts. Both crypto owners and traders have to be aware of malware development. Clipboard injector malware has already made a clean sweep of Bitcoins, Litecoin, Ethereum, Monero and Dogecoin. Traders in more than 52 countries have been affected.
How does it operate?
- The cybercriminal downloads the Tor browser a trojan version via a 3rd party.
- It is a password-protected RAR archive file.
- Password avoids the security apparatus and the file infilters into the victim’s system.
- It has a masked icon and is activated when the computer restarts.
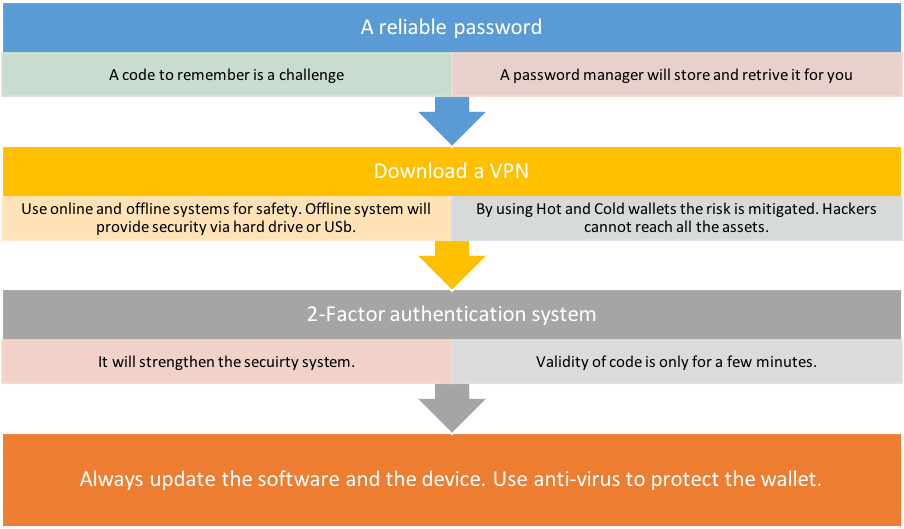
Best practices to mitigate the vulnerability
Like with every other asset the crypto wallet needs protection with the best practices. When you choose a wallet service from the exchange, they give a unique seed phrase. It helps to recover the wallet. This is very private to the user and should be stashed away offline.
The vulnerability increases by the following methods
To protect the wallet these steps should be taken.
If you are keen on setting up a wallet of your choice? Let us know. We keep sharing valuable information for users to trade without any vulnerability. Remember it is important to understand the crypto wallet types to avoid hackers.
